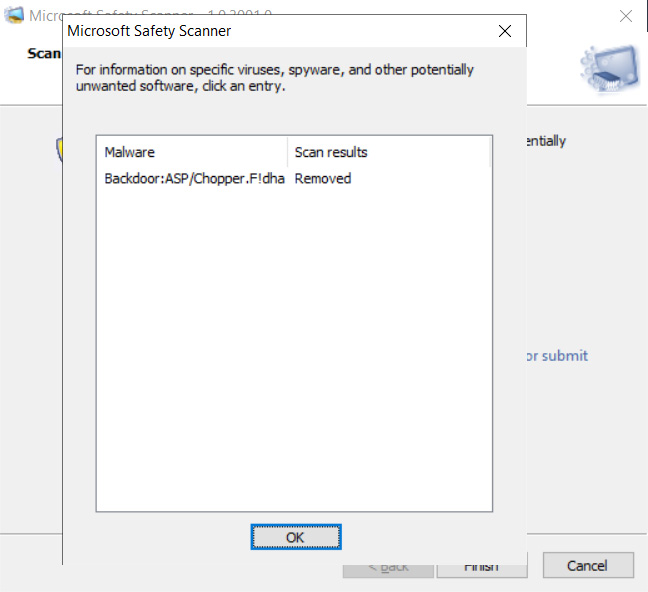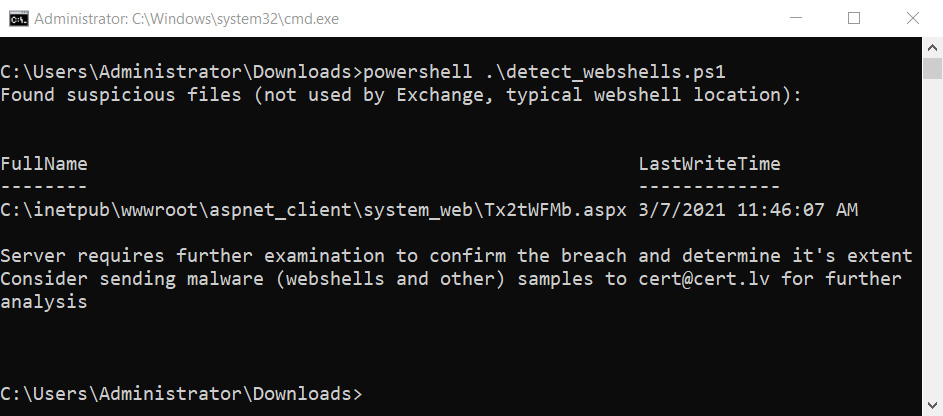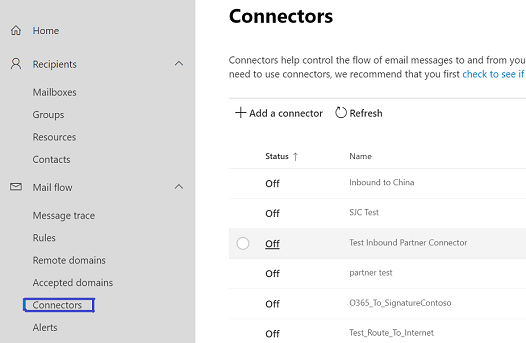
How to set up a multifunction device or application to send email using Microsoft 365 or Office 365 | Microsoft Learn

SOLVED: How To Setup SCAN TO EMAIL Using Office 365 on Ricoh Copiers | Up & Running Technologies, Tech How To's
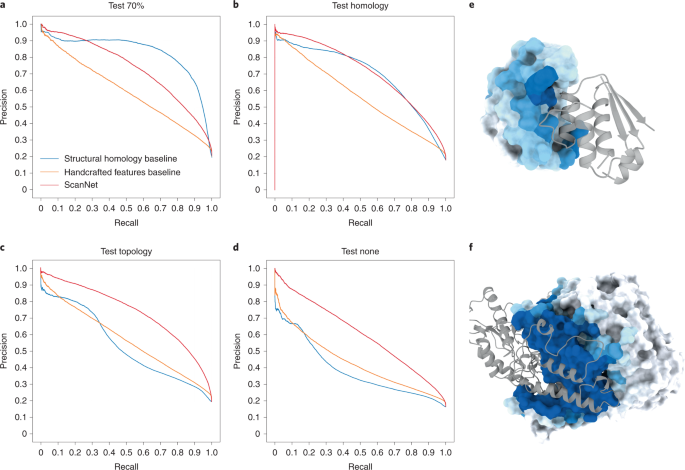
ScanNet: an interpretable geometric deep learning model for structure-based protein binding site prediction | Nature Methods