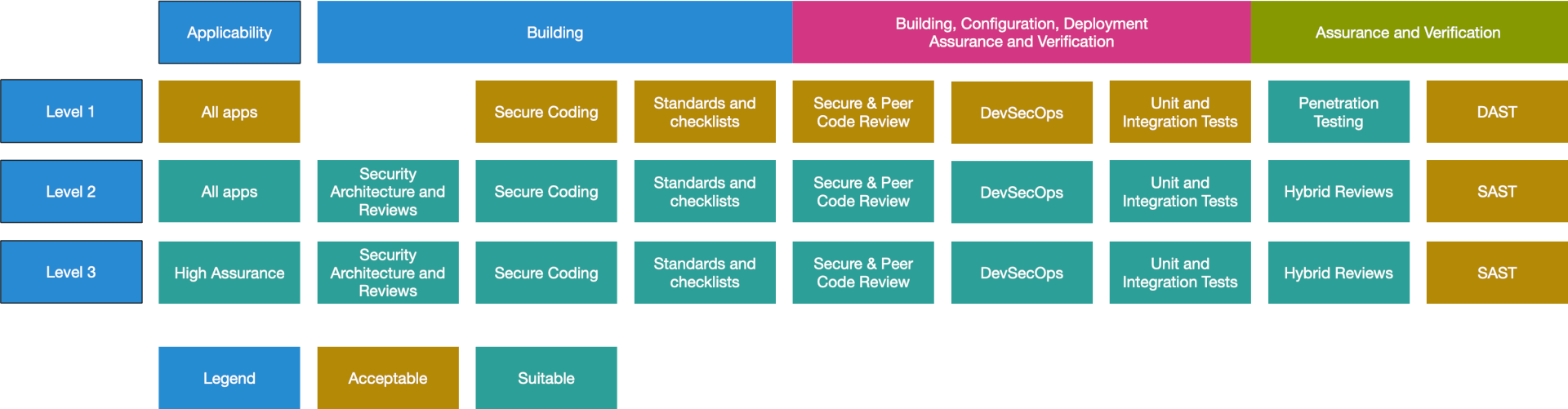
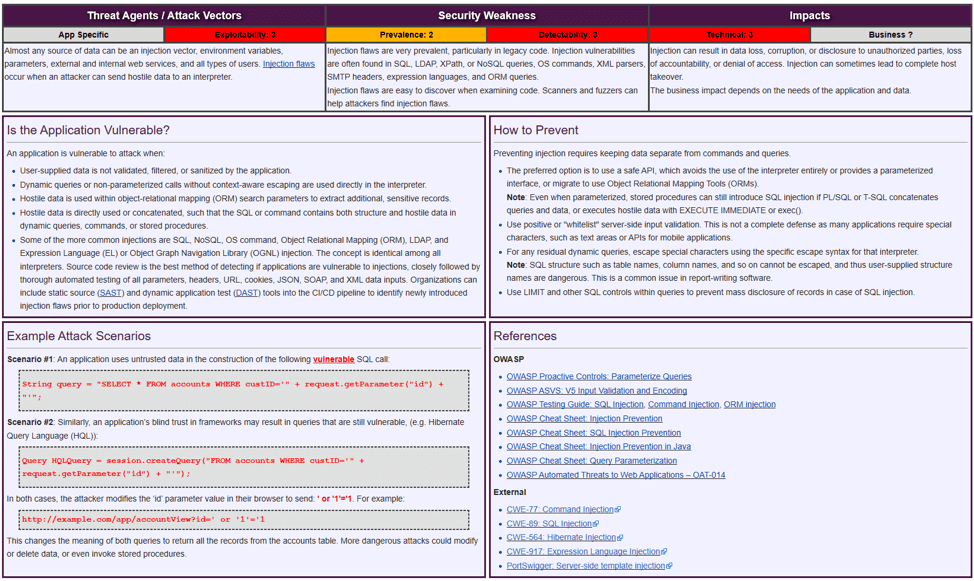
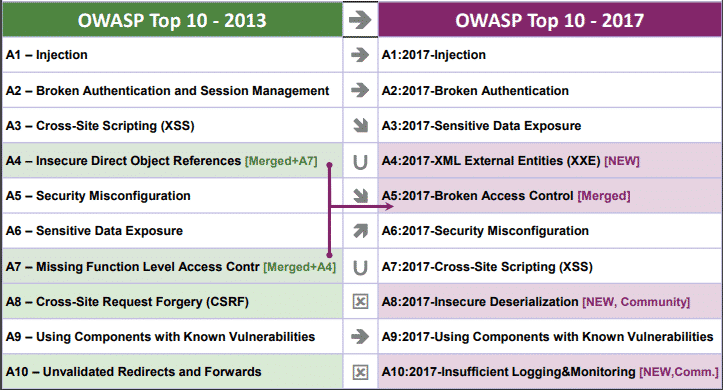
Hacker Combat - The goal of the OWASP Top 10 Proactive Controls project (OPC) is to raise awareness about application security by describing the most important areas of concern that software developers

OWASP Top 10 Proactive Controls and Exploits - Part 1 - Foundational Topics in Secure Programming | Coursera

Snyk on Twitter: "Check out our takeaways from @manicode's #OWASP Top 10 Proactive Controls https://t.co/rXxECpVcrb https://t.co/2nGbuNv4sc" / Twitter